Cyber security experts are warning that the partial government shutdown could create an opportunity for cyber attacks because critical IT functions are not being maintained as a result of furloughed government employees.
With thousands of government IT workers furloughed as a result of the standoff between President Trump and congressional Democrats over border security, more than 80 security certificates used by .gov websites have expired. Sites affected include the Department of Justice, NASA, and the Court of Appeals. Some of the affected websites can no longer be accessed due to security protocols implemented before the shutdown and others are displaying a security warning when users attempt to access them.
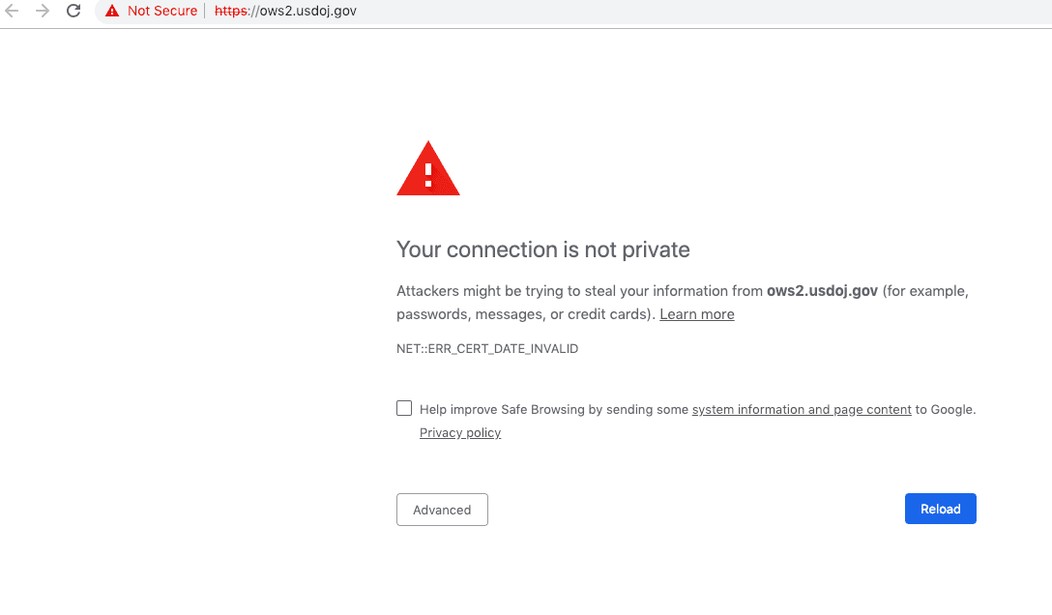
A Department of Justice website (https://ows2.usdoj.gov), for example, was using a certificate that expired on December 17 and has not been renewed. Visitors to the site are greeted by a warning message indicating that the site is not secure:
A U.S. Court of Appeals website (https://ecf-test.ca6.uscourts.gov/) warns, “Your connection to this site is not secure.” The message tells users not to enter any sensitive information but does allow them to disable the security warning and proceed to the site.
A secure sockets layer (SSL) or transport layer security (TLS) is the standard technology that keeps an internet connection secure and protects sensitive data that is transferred between two systems using an encryption algorithm. It prevents bad actors from reading or modifying data like credit card numbers and identity information as it is being transmitted. “HTTPS” in a website’s URL rather than “HTTP” indicates that a website can be trusted — the “S” stands for secure. Certificates verifying the security of a site are issued by a trusted certificate authority and come with an expiration date that requires them to be periodically renewed. When a certificate is expired, an attacker can trick your browser into believing it is visiting a secure site and then redirect you to a non-secure website where your personal information can be intercepted. All federal websites accessible to the public are required to have a secure connection with a valid security certificate.
The usdoj.gov domain — and all of its subdomains — is part of the HSTS (HTTP strict transport security) preload list, an enhanced security measure that prevents users from visiting an HTTPS site if the certificate is expired. In those cases, users aren’t offered the option to bypass the warning message and continue on to the site.
A NASA site (https://rockettest.nasa.gov/), which is not included in the HSTS preload list, carries a certificate that expired on January 5. Users are given a warning message noting the security risk but are free to ignore that message and continue on to the unsecure site.
“Until US Congress resumes services it is inevitable that we will see expired certificates and this example just goes to show how vulnerable organizations who are susceptible to shutdown can be,” said Paul Tourret, managing director at GlobalSign, a trusted certificate authority company.
Netcraft’s Paul Mutton, who discovered the expired government security certificates, explained, “As more and more certificates used by government websites inevitably expire over the following days, weeks — or maybe even months — there could be some realistic opportunities to undermine the security of all U.S. citizens.”
At the tech website rud.is, a blogger with the user name “hrbrmstr” ran a query and found that another 26 certificates are set to expire before the end of January, meaning the problem will only get worse. “Not every agency is fully shutdown and not all workers in charge of cert renewals are furloughed (or being forced to work without pay),” he wrote. “But, this one other area shows the possible unintended consequences of making rash, partisan decisions (something both Democrats & Republicans excel at).”
Patrick Nohe, editor-in-chief at Hashed Out, warned this week that the partial government shutdown “is doing serious damage to the US cybersecurity apparatus” and said the long-term impact could be even worse.
The Cybersecurity and Infrastructure Security Agency (CISA), which is part of the Department of Homeland Security, “has effectively been knee-capped by the shutdown,” Nohe said, as has the National Institute for Standards in Technology (NIST).
“Right now, 45% of the Cybersecurity and Infrastructure Security Agency is furloughed. 45% is also the percentage of employees on the DHS’ analysis and operations teams – comprised of the Office of Intelligence & Analysis, and the Office of Operations Coordination – that are furloughed, too,” he wrote. “The National Protection and Programs Directorate – which handles a range of functions like the US-CERT (US – Computer Emergency Readiness Team) Continuous Diagnostics (CDM) and Automated Indicator Sharing (AIS) programs – has a whopping 85% of its workforce furloughed. ”
“And beyond that,” Nohe wrote, “even at full strength the US cyber defense apparatus is being pushed to the brink by foreign, state-sponsored hackers and cyber cells. So weakening it puts the whole country at greater risk.”











Join the conversation as a VIP Member