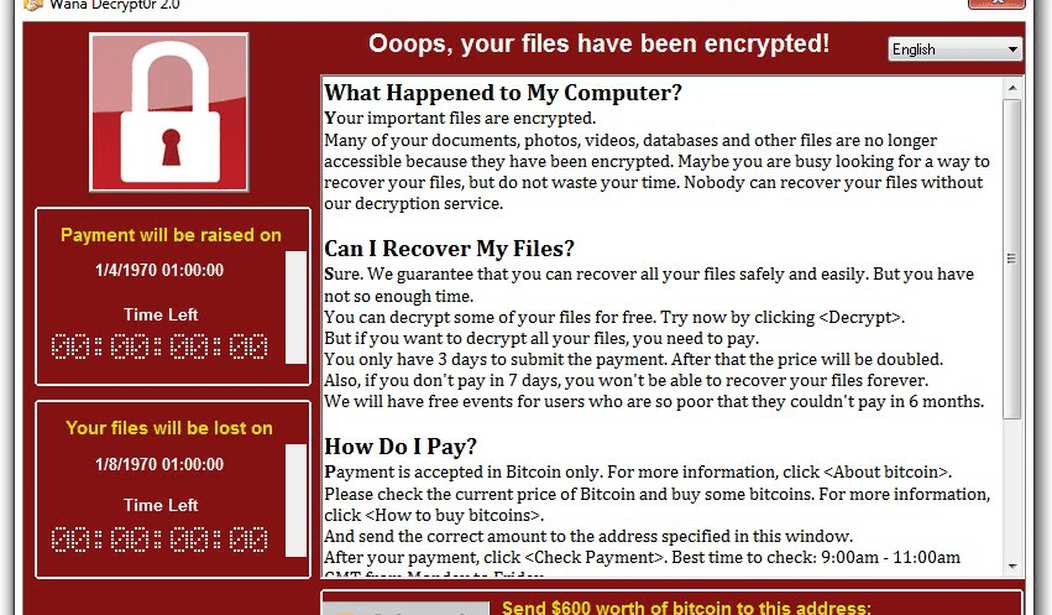
Cyber security experts around the world are bracing for new attacks on computer systems from a worm that crippled tens of thousands of machines over the weekend. New variations of the virus dubbed WannaCry are expected despite a lowly researcher’s intervention on Friday that supplied a temporary fix to the problem.
Microsoft released patches last month and on Friday to fix a vulnerability that allowed the worm to spread across networks, a rare and powerful feature that caused infections to surge on Friday.
Code for exploiting that bug, which is known as “Eternal Blue,” was released on the internet in March by a hacking group known as the Shadow Brokers. The group claimed it was stolen from a repository of National Security Agency hacking tools. The agency has not responded to requests for comment.
Hong Kong-based Ivezic said that the ransomware was forcing some more “mature” clients affected by the worm to abandon their usual cautious testing of patches “to do unscheduled downtime and urgent patching, which is causing some inconvenience.”
He declined to identify clients who had been affected.
The head of the European Union police agency said on Sunday the cyber assault hit 200,000 victims in at least 150 countries and that number will grow when people return to work on Monday.
“At the moment, we are in the face of an escalating threat. The numbers are going up, I am worried about how the numbers will continue to grow when people go to work and turn (on) their machines on Monday morning,” Europol Director Rob Wainwright told Britain’s ITV.
MONDAY MORNING RUSH?
Monday was expected to be a busy day, especially in Asia which may not have seen the worst of the impact yet, as companies and organizations turned on their computers.
“Expect to hear a lot more about this tomorrow morning when users are back in their offices and might fall for phishing emails” or other as yet unconfirmed ways the worm may propagate, said Christian Karam, a Singapore-based security researcher.
Targets both large and small have been hit.
Renault said on Saturday it had halted manufacturing at plants in Sandouville, France, and Romania to prevent the spread of ransomware in its systems.
Among the other victims is a Nissan manufacturing plant in Sunderland, northeast England.
Hundreds of hospitals and clinics in the British National Health Service were infected on Friday, forcing them to send patients to other facilities.
German rail operator Deutsche Bahn said some electronic signs at stations announcing arrivals and departures were infected.
No one knows who is behind the attacks. The fact that the ransom asked for is between $300 to $600 suggests an unsophisticated group of criminals picking targets of opportunity. An organized crime syndicate would probably be asking for a lot more.
Needless to say, don’t open any email from an unknown sender and definitely don’t click on any links contained in suspicious emails. These commonsense precautions were apparently ignored by many thousands of people which caused the rapid spread of the virus.
I suppose this is something we’ll have to get used to as criminals become ever more adept at penetrating computer systems to wreak havoc on our electronic world.









Join the conversation as a VIP Member